How to Set Up a Proxy Server: Configuration Instructions
Learn how to set up your proxies on various devices, operating systems, and apps.
Proxy servers are a tool. They can help you filter traffic, improve anonymity, access geo-restricted content, and scrape the web.
You might be new to proxies, or simply looking for instructions on how to set them up for a particular tool. This page guide you to an explanation on how to setup a proxy server with various operating systems, browsers, and apps. The guides will feature illustrated step-by-step instructions to make your proxy setup simple and straightforward.
If you didn't find the integration instructions you were looking for, contact us and we’ll add them to the list.
Proxy Configuration Instructions
Set Up a Proxy on an Operating System
Enabling a proxy server on an operating system will make all your connection requests go through a proxy. In other words, the settings apply system-wide unless you override it in some way.
Set Up a Proxy on a Web Browser
There are several reasons why someone would want to set up a proxy on a web browser instead of an entire operating system. For example, you might need to route web browser traffic through a proxy to access geo-restricted web content, but still want a direct connection for a multiplayer game.
If you want to use and manage proxies with a browser extension instead, you can find the tutorial here:
Set Up a Proxy with Web Scraping Libraries
Web scraping needs proxy servers to overcome IP blocks and other restrictions. Some integrations are relatively straightforward, while others, often involving headless browser libraries, require workarounds.
Set Up a Proxy on Applications
You can also use applications like Proxifier to configure your proxy settings to allow apps that support proxies to route their data via one..
We have a guide on how to use the application and multiple ways to configure proxies with it.
General Information on How to Use Proxies
Understanding a Proxy Server Address
Whether you’ve bought proxies or found a list online (we don’t recommend using free proxies, by the way), a proxy server consists of three main elements: protocol, address, and port.
1) The protocol determines what kind of content you can access. HTTP and HTTPS support website traffic; HTTPS is safer because it encrypts the information you send. The SOCKS protocol allows accessing more diverse content, such as torrents or SMTP.
2) The address functions like a street address for the internet; this is how you connect to the server. The proxy server’s address can look like a regular IP (192.168.0.1) or use a DNS hostname and look like a regular URL (en.proxyprovider.net).
3) The port number indicates what type of data the proxy server is to accept. It doesn’t reflect which ports the proxy server actually has open – you’ll have to find that out from your provider.
So, here are the two formats of a proxy IP address you’re most likely to encounter:
- 192.168.0.1:10000
- en.proxyprovider.net:10000
Proxy Authentication Methods
If you’ve bought access to private proxies, you’ll need to authenticate – basically log in – to use them. There are two main ways to do it and only some proxy providers support both:
1) Credentials simply refer to a username and password. Proxy manager apps may have separate fields for them or require appending the credentials to the proxy IP address. In the latter case, the address would look like this: 192.168.0.1:10000:username:password. If your proxy server is asking you for a password, you most likely haven’t entered the credentials.
2) IP whitelisting lets you specify an IP address that can access the proxy server. This method isn’t ideal if you have a dynamic IP (there are workarounds) but it doesn’t modify the proxy’s IP address and doesn’t require any other fields like credentials.
What happens if you’re not authenticated? The proxy server won’t let you access any content. Instead, you’ll get the proxy server is refusing connections or the 407 error.
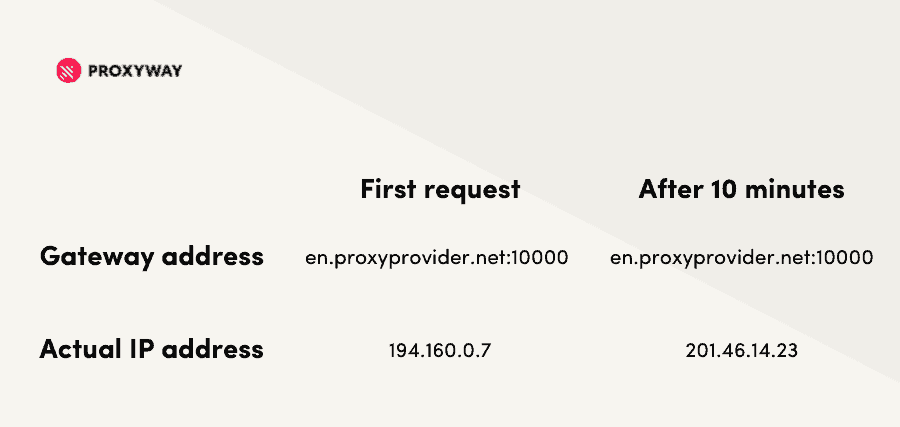
Working with Rotating Proxy Servers
Unlike proxy lists, which have a separate address for each IP, rotating proxies often use backconnect gateway servers. These servers provide one hostname and allow you to access different IPs by changing the port number or adding parameters to the username. After a while (it depends on the provider’s settings), the IP rotates; the gateway server remains the same.