Fighting IP Hijacking: Interview with Stat Proxies
Nicholas St Germain shares his experience in stopping unauthorized IP use for proxies.
- Published:

Your Twitter profile states that you’ve been “a proxy guy since 2017” – a long time for this space. Can you briefly tell us your story?
“As a sneaker botter, I initially had to buy proxies from others, but the costs were adding up. I decided to learn how to create my own proxies to save money and improve my setup. Ultimately, that led to selling proxies to others.
I began with data center proxies, which worked well for a while, especially in the sneaker botting space. However, I needed to adapt as these sites implemented more sophisticated antibot measures. This initial phase gave me enough time to build up capital, acquire domain expertise, and invest in a colocation facility to create what we call ISP proxies today.
My company at the time, Dash Proxies, grew steadily and eventually merged with Stat Proxies. I helped create and expand the B2B side of Stat Proxies, and today I continue to focus primarily on the B2B market, working with a wide range of companies and customers.”
You also write that, among other things, you do something called IP hijacking prevention. What exactly is IP hijacking and how does it work?
“IP hijacking is essentially the act of stealing access to IP address assets. A malicious user finds a way to get an IP block announced on a network. Hijackers then use those IPs for their nefarious purposes or sell them to unsuspecting buyers. There are various methods to accomplish this, and I’ll discuss those in more detail later.”
IP hijacking prevention isn’t really an ordinary activity – for us, at least. What motivated you to start doing it?
“I was a victim of a hijacker who went by the name of “Thrace.” I had no idea what was happening until Charlie, who I now work with on Stat Proxies, sent me a message one day warning me of what was happening.
Once I figured out how these threat actors operate, I did everything in my power to stop them. I’m passionate about doing right by this community and want to help where I can. This was back in early 2021, and even now, three years later, I still shut off his IPs when I find them.”
What are the usual IP hijacking targets? Have you noticed a particular type, or is it rather anyone vulnerable?
“I’ve seen all types of targets, but some stand out more than others. When companies merge or go out of business, their IP resources often get orphaned, making them prime targets for IP hijackers. These hijackers can buy the company domain once it expires and gain access to their ARINⓘ account, giving them the ability to do almost anything with those IPs.
Sometimes, organizations don’t have a use for their IP space and fail to monitor it. A great example of this is when a school district had a /18 block (16,384 IPs) hijacked. When I contacted their IT team, they had no idea this was happening and mentioned they hadn’t touched anything related to that IP space in years.
In other cases, hijackers don’t even need access to an ARIN account. For example, Internet service providers have large IP blocks announced, such as a /14 (262,000 IPs). Hijackers can create falsified documents and use free IRR databasesⓘ to reflect these fraudulent documents. Some of these free databases mirror into more reputable databases.
Some data centers and hosts don’t require protections like RPKIⓘ or ROAⓘ to be set via the ARIN account, making it easier for hijackers to use these documents to get IPs announced.
In conclusion, if you do not set RPKI/ROA on your ranges, you are leaving yourself open to being hijacked. RPKI/ROA adoption is trending in the right direction, but there are large blocks of legacy IPv4 resources that do not support RPKI/ROA.
It is important to note that many of the ranges being hijacked were allocated 20+ years ago and do not have membership with ARIN. If there is no valid membership with ARIN, RPKI/ROA is not able to be set. The owner would have to begin paying ARIN fees. That’s why you will see few ISPs setting these measures on their ranges, as it is quite expensive to hold millions of IP addresses with ARIN.
Below is a real Letter of Authorization that a Hijacker created, but none of it is legitimate.”
How widespread do you think IP hijacking is?
“I have shut down somewhere between 750,000 and 1,000,000 IPv4 addresses over the past four years, most belonging to Thrace. I think hijacking is much bigger than the few individuals I have targeted.
You’ll find hijacked IPs mostly in the black hat areas, such as account cracking. You can find these IPs in almost any industry, though. I have seen fewer U.S. network operators accepting hijacked IPs into their networks nowadays compared to the previous years.
Any company or individual can have their IPs hijacked from them. I’ve dealt with IPs ranging from U.S. defense contractors to simple mom-and-pop shops.”
Let’s talk about practical matters. How do you identify hijacked IPs, and what do you do then?
“There are many different ways I have encountered hijacked IPs. Many people know that I am extremely passionate about shutting down stolen ranges, so they send me ranges to check if they have any suspicions. I also routinely monitor ASNs that hijackers have used in the past (they are constantly using the same ones). It’s important to note that sometimes I see actual ASNs hijacked as well. Usually, they are 4-digit ASNs ranging from 6xxx to 7xxx. Don’t ask me why that range specifically, as I have no clue!
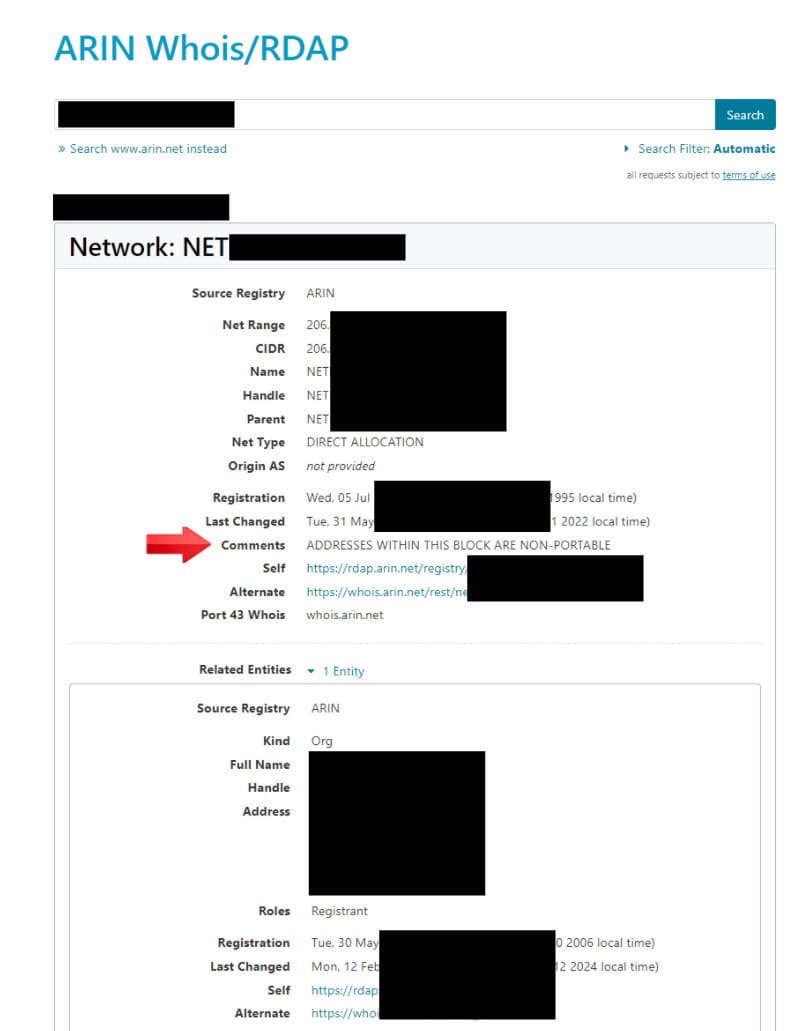
Once I have an IP range, there are many different things to check. If it is a range owned by a large international telecom, I will check the ARIN WHOIS and see if it is listed as non-portable. This means the ISP is explicitly saying it should not be subdivided into multiple ranges or used on a different network besides those explicitly listed. That is usually the easiest way to tell. If you have a range like this and it is being announced on XYZ Inc., it is likely being hijacked.”
“You might be asking yourself, what happens when the range is announced on two different networks at the same time? In this specific case, when RPKI/ROA is not involved, the smaller announcement will always take priority in the routing table, enabling the hijacker to use the IPs.
Another case you will see is when the IP space has not been announced for many years (think 8+) and randomly appears on a new network never used before. Combine that with an outdated ARIN account and inactive company – you likely have a hijacking happening.
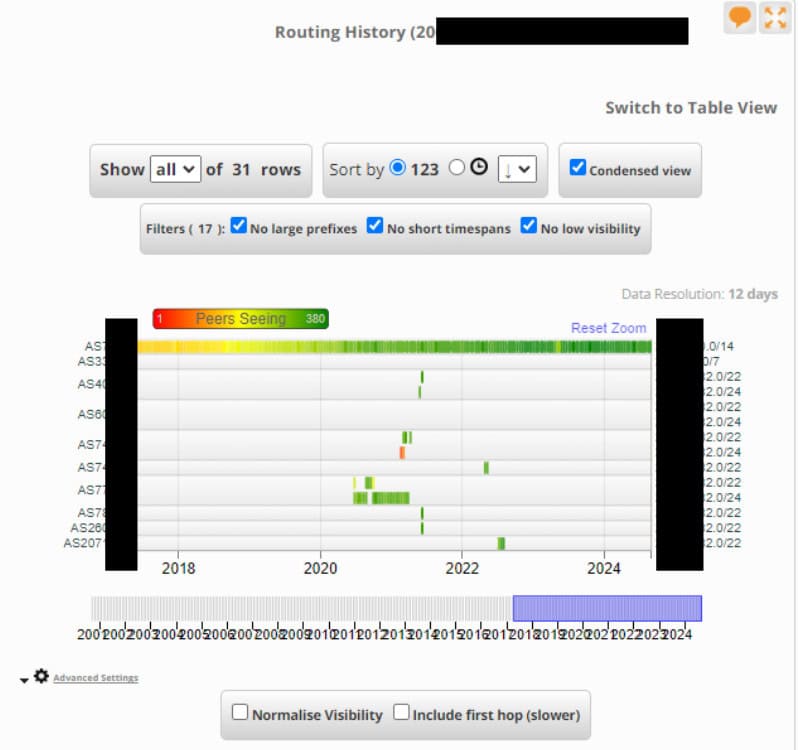
My favorite method is using past resources used by hijackers. I have a database of known hijacked ranges, ASNs, accounts on IRRs, etc. The above picture shows that the same range was used for almost three years across different networks. Thrace used the same IRR maintainer for over 2 years and would add new IP ranges every time I shut down his IPs.
That made my life so easy! Eventually, I went on to have that account shut down by that IRR. It ended up having nearly 300 different ranges listed with it!”
How do the targets usually respond once you contact them? Have you received any rewards for your efforts?
“Unfortunately, I do not get to speak with the IP owner as much as I would like. It is challenging to contact these people as the contact information is old or the company itself is too large to get ahold of someone who understands what is happening.
Most of my work goes towards messaging the actual host, providing all of the evidence, and hoping that works. If it doesn’t, I go to the upstreams of the host and inform them. That usually works well. Most hosts do not want hijacked IPs on their network as it ruins their reputation, so they usually act quickly.
I have been able to contact some owners of hijacked IP space, and they are always super grateful. From what I remember, the only time I received something from a target was a free domain (they were the owners of a semi-large domain name company).”
It sounds like you treat IP hijacking prevention as more of an extracurricular activity – like volunteering. Are there any other projects you’re working on?
“Absolutely! I really do enjoy doing this work and am not doing it for any reward or compensation. Currently, I spend most of my time building Stat Proxies. We offer static residential ISP proxies to companies for all different types of use cases, from purchasing products to collecting internet data at scale. You can learn more about us here.
If you have any questions about IP hijacking, message me on Twitter/X @nickfromstat, and I will do my best to answer!”